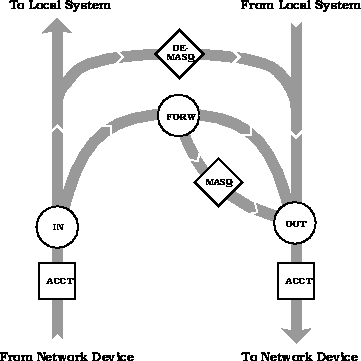
Figure 3
In Linux, IP traffic can be counted using accounting rules, defined by the same characteristics as the firewall rules. Accounting is done at two places: when a packet is received and when a packet is sent out (see figure 3).

Figure 3
So, a packet being forwarded is counted twice: the first time just after its arrival, the second time when it is being sent out again. There is one single list of accounting rules, that is being used for both incoming and outgoing traffic. For every packet, all rules in this list are checked and the packet and byte counters of every matching rule are incremented. Note the difference with the firewall lists: scanning a list there stops at the first match.
The following ipfwadm command counts all http traffic related to people using your WWW-server from the outside:
ipfwadm -A -a -b -W eth1 -P tcp -D 192.168.37.1 www
Here it is assumed that the local system, hosting the WWW-server, has IP address 192.168.37.1. We see some new options in this command. The -b option means ``bidirectional'', and makes that also packets coming from 192.168.37.1 (port 80) are counted. In general, think of the same rule with -S and -D swapped. The -W option has an interface name as parameter, so that only traffic via that particular interface is taken into account. Packets passing another interface (e.g., an interface eth0 connected to your internal network) are not counted here.
Although there is only one list of accounting rules, used in both directions, it is possible to let a rule match only with incoming or outgoing packets:
ipfwadm -A in -a -W eth1 -P tcp -D 192.168.37.1 www
ipfwadm -A out -a -W eth1 -P tcp -S 192.168.37.1 www
The desired direction, in, out, or both, can be specified after the -A option. The default direction is both.
Some suggestions to use accounting most effectively:
When listing the accounting rules (and the associated values) with ipfwadm, the pseudo-file /proc/net/ip_acct is read.
Copyright © 1996 by X/OS Experts in Open Systems BV. All rights reserved.